If you have any hunting experience or have been in a beer talk with hunting stories you probably have came across the term “Watering Hole Attack“. In this attack the hunter is covered near an area with a water hole where animals go in order to drink water, feel safe and usually have their guards down and their instincts more relaxed. So they don’t have to track the prey and attack on the go but wait until it comes to it’s fate on it’s own. Very similar to this approach a hacker targets specific end users by infecting frequently visited websites with malware that spreads to the user’s device.
How is it done
The target victim can be an individual or a group of people belonging on an organization or have similar interests like for example have accounts in the same bank.
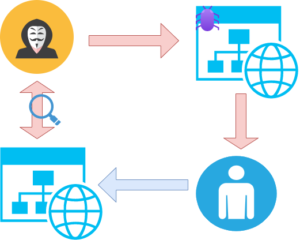
The attacker profiles the targets, scanning mostly their social activity, to determine the type of websites they frequent. These are often messaging boards or general interest sites popular with the intended target. They will look for a known vulnerability on the website, compromise the site, and infect it with their malware before they lie in wait for baited users to attack.
Attackers will even bite users to visit the sites by sending them emails directing them to specific parts of the compromised website. The problem is that often, these emails do not come from the attackers themselves, but through the compromised website’s automatic email notifications and newsletters that go out on a constant basis. This makes detection of the email lures very difficult.
After the visit, typically the user’s machine is transparently compromised via a drive-by download attack that provides no clues to the user that his or her machine has been attacked and corrupted.
The attacker then can use the victims computer either to exploit him, get information, launch other attacks etc.
This makes defending against watering hole attacks quite difficult for organizations. Without protection against these attacks, websites can be infected for months or even years before they are detected.
Known Major Attacks
- In 2021, threat actors used the “Live Coronavirus Data Map” from the John Hopkins Center for Systems Science and Engineering to spread malware among users nationwide.
- In 2016, the Canada-based International Civil Aviation Organization (ICAO) was breached with similar methods and spread malware that infected the United Nations (UN) network.
In 2014, a foreign attack group hacked Forbes.com and used similar strategies to target visitors working in the financial services and defense industries. - In 2013, hackers breached the United States Department of Labor website. The attackers used the website to redirect visitors to a malicious site hosting malware.
How to defend
- Always use an antivirus and internet security software. If a website is compromised, it wont be long that a web scanning engine will detect it. If you use an internet security software it will warn you regarding the infection.
- Use a Virtual Private Network (VPN). A VPN can disguise online activity from external sources, making it harder for attackers to profile you.
- Monitor Your Network and Web Traffic. Internet Monitoring your network activity and all web traffic coming from outside can help prevent watering hole attacks. It can identify malicious activity and abnormalities that can indicate an attack.
- Always update your system. Watering hole attacks exploit vulnerabilities in your software. Keeping your software up to date it will reduce these potential vulnerabilities.
- Treat all automated email as untrusted. Prefer to visit a site your self rather than follow a link on an email.