In this tutorial, we’ll explore the database modeling aspect of a small blog using PlantUML. We’ll start by defining the tables and their attributes, then establish relationships between them based on the provided database model.
1. Understanding the Database Model
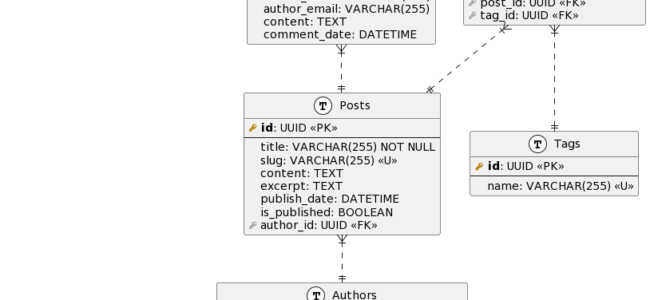
Let’s review the database model for our small blog:
Tables:
- Posts: Represents individual blog posts.
- Users: Stores user information for blog authors.
- Comments: Contains comments left by users on blog posts.
- Tags: Stores tags associated with blog posts.
- PostTags: Join table to establish a many-to-many relationship between posts and tags.
Relationships:
- Posts – Users: One-to-many relationship where a post belongs to one user.
- Posts – Comments: One-to-many relationship where a post can have many comments.
- Posts – Tags: Many-to-many relationship facilitated by the PostTags join table.
- Tags – Posts: Many-to-many relationship facilitated by the PostTags join table.
Continue reading “Database Modeling Tutorial Using PlantUML”